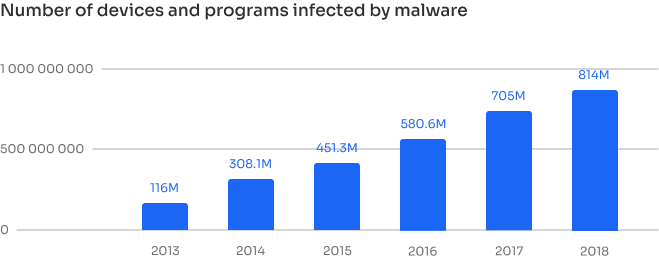
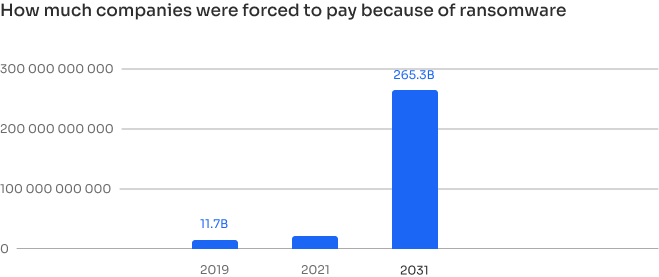
Malware
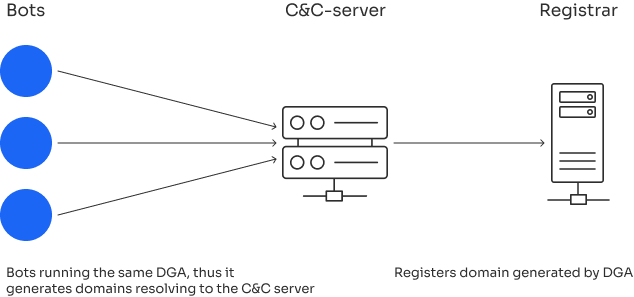
Malicious software that aims in one form or another to cause damage to the user or computer and its contents. Malware is a common group for all types of cyber threats, such as viruses, Trojans, spyware, keyloggers, adware, etc.
What harm can Malware do to your network or device?
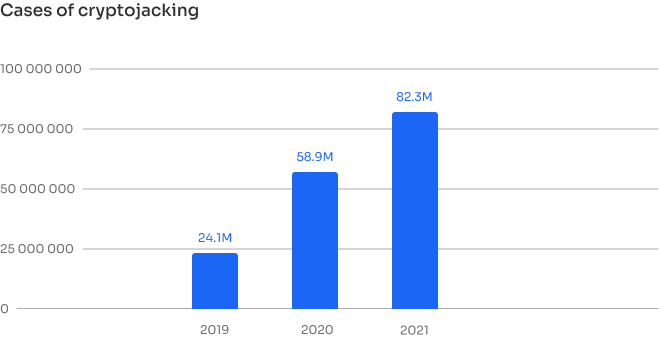
Malware creates a lot of problems for the user - from small almost imperceptible inconveniences to serious financial harm. Form example, change the browser settings and do not allow the user to change them, waste computer resources, thereby reducing its performance, install advertising programs on your computer, such as pop-ups and banners that work even without an Internet connection, use a computer and its resources for DDoS attacks or cryptocurrency mining and collect user’s personal data: usernames, passwords, bank card numbers, etc.
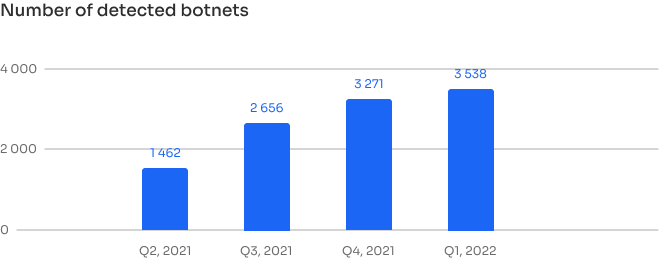
Companies spend the most money on protection against malware:
about $2.4 million.